Difference between revisions of "Brute-force attack"
From SFPTotal Wiki
| Line 9: | Line 9: | ||
# Change at least one byte in the HEX grid. The code in software's window should be different than a code in transceiver's memory | # Change at least one byte in the HEX grid. The code in software's window should be different than a code in transceiver's memory | ||
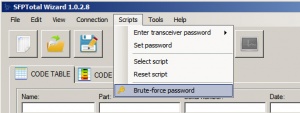
# Open menu '''Control -> Search password''' | # Open menu '''Control -> Search password''' | ||
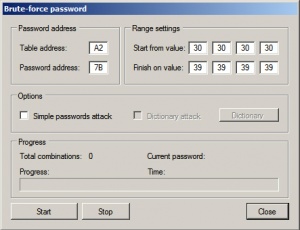
| − | # Set | + | # Set parameters Table address (default: A2) and Password offset (default: 7B) |
| − | + | ||
# Set additional options (if needed) | # Set additional options (if needed) | ||
| + | # Select range of password value or use dictionary of passwords | ||
# Push '''Start''' button to begin brute-force attack | # Push '''Start''' button to begin brute-force attack | ||
== Example == | == Example == | ||
<youtube>https://www.youtube.com/watch?v=q04PfsST3Xk</youtube> | <youtube>https://www.youtube.com/watch?v=q04PfsST3Xk</youtube> | ||
Revision as of 17:41, 26 July 2018
For password recovery SFPTotal Wizard supports a search function in brute force mode. This function could help if you need check passwords in a narrow range of values. Also, you can fast check a password for write-protected transceivers using a dictionary of passwords.
How to use
- Read a vendor code from transceiver (or use random code template)
- Change at least one byte in the HEX grid. The code in software's window should be different than a code in transceiver's memory
- Open menu Control -> Search password
- Set parameters Table address (default: A2) and Password offset (default: 7B)
- Set additional options (if needed)
- Select range of password value or use dictionary of passwords
- Push Start button to begin brute-force attack
Example